In which, the vehicle first selects random number as the temporary short time private key(x) and then takes a point on the elliptic curve (G) using that computes corresponding temporary short time public keys(P) as: P = x*G
Signature Generation: In order to preserve integrity of message M, vehicle generate short time anonymous signature using HMAC-SHA256 algorithm and private key. The vehicle first calculates hash of the message using HMAC-SHA256 algorithm and then map the hash value to a point on an elliptic curve as H(M). The signature of the message is then computed as, S = x*H(M)
Prioritazation, Verification and reducing authentications: The vehicle sends message, signature and public key to RSU as msg = (M || S || P), the msg is prioritize depending on the type of message M. Types of messages sent to RSUs are:
Message from ambulance and fire brigade. Accident message from particular vehicle. Traffic jam message.
Normal authentication message.
In which, 1 has highest priority while 4 has lowest priority.
The vehicle is authenticated at RSU if e(G,S) = e(P,H(M)) holds true else it is a malicious vehicle and is reported to TA by RSU. The integrity of message is also checked using HMAC-SHA256 algorithm. All this verification code is in the smart contract.
Consider a vehicle V1 in the range of RSU1 and is intended to travel towards RSU2. The vehicle is authenticated at RSU1 and is assigned with timestamp based on highest distance required to travel its neighbouring RSUs i.e. RSU2, RSU3 and RSU4 along with some time delay due to external factors.
The vehicle information is then broadcast to its neighbouring RSUs. If the vehicle is able to travel the distance in the given timestamp into the range of RSU2, it is not authenticated again.
The RSU2 just pass the message to the vehicle that it is an authenticated vehicle and there is no need of authentication again. But if the vehicle fails to travel the distance within the given timestamp into the range of RSU2, the RSU2 will send authentication request to vehicle and the vehicle will be authenticated again.
Tracking: The useful messages are stored by RSU in blockchain by using PoA in the form of a transaction. In case of dispute, TA track real identity by looking into its local database and blockchain database. After tracking the real identity, the TA revoke the privacy of the malicious vehicle or RSU from causing any further damage.
Performance Analysis
Fig.2 shows the comparison between time at which authentication of nth vehicle is completed by existing system and proposed system. For existing system, as number of vehicles at particular RSU increases, the authentication time increases linearly. When vehicles enter the range of RSU, they are queued at RSU to complete authentication process. Each vehicle is treated the same hence, emergency vehicles such as ambulance, fire brigade, etc. and emergency message such as accident message get delayed.
As fixed time is required to authenticate the vehicle, the graph is linear and time delay increases as number of vehicles increases. In proposed system, if a vehicle is authenticated at one RSU and it covers distance to another RSU in given time then, the RSU will send authentication successful message to vehicle hence, there is no need of re- authentication and queuing at RSUs. If vehicle fails to cover certain distance in given time then it will be queued and re- authenticated at RSU also, the emergency vehicles are prioritized based on message received at RSU.
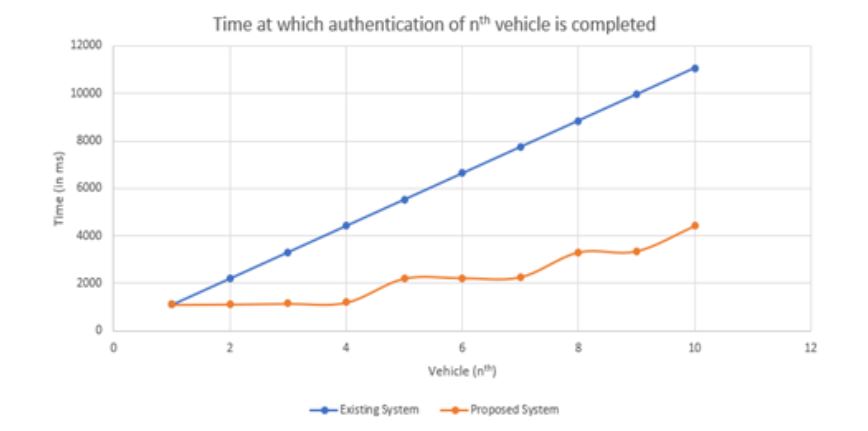
Figure 2: Time at which authentication of nth vehicle is completed
In existing system, after authentication completion of one vehicle, next vehicle’s authentication begins. While authenticating certain vehicle, by that time no other vehicle can be authenticated. In the graph, the point represents time at which authentication of nth vehicle is completed while, the line represents authentication is in process.
Hence, the graph is linear. For proposed system, as private ledger stores the information from neighboring RSUs of already authenticated vehicles and their timestamp, while authenticating 2nd vehicle, 3 vehicles arrives in that time which are already in private ledger and within timestamp then that vehicles receives authentication successful message at the time at which they enters into the range of RSU. So, there is no need of queuing and reauthentication for that 3 vehicles and hence, for 2nd vehicle after completing the authentication process it is authenticated as 5th vehicle. In this way, the number of authentications is reduced.


 ©
©